How to Hack Chinese (Watch) Phone Firmware
This page is intended to explain how to hack pre-Android Chinese phones based on the MediaTek MT62xx platform, running the ‘Nucleus’ operating system. The hacks focus on watch phones, but the principles are the same for all phones based on the same hardware platform. If it is not obvious from the length of the page and the amount of technical terms in the descriptions, hacking these phones is not easy. You cannot just download some easy-to-use app, you cannot really ‘root’ the phone like on Android, and you cannot just edit a few files to make groundbreaking changes.
This Hackaday article, as well as this bunniestudios blog post, give a hint at why hacking this platform is so frustrating: the Chinese do their best to keep it a gated community only accessible to Chinese companies. Only within China, there is quite a bit of openness about the hardware even though officially it is all supposed to be confidential. (This practice is called ‘Gongkai’ or 公开 in the bunniestudios article.) In the West, all we can do is use the scarce leaked documents we can find (possibly after translating them), and for the rest it is a matter of tedious reverse engineering.
Please do not waste your and my time by mailing me with vague and general questions about how to hack any generic Chinese phone, I won't even reply to such mails. All the essential information I can tell you is already in this page, and more clarification can often be found by using a search engine. Some examples of good reasons to mail me are asking clarification for something explained here, or asking how to find a particular file inside the ROM dump.
Also, please do not ask me to perform one of these hacks for you. I will not do it. Not even if you're willing to pay for it. Any mail containing such a request will be ignored, so don't waste your time and hope on this. I have grown so sick of hacking this god awful proprietary MTK platform, that I refuse to touch it anymore. In general I recommend to avoid these Nucleus OS-based phones and use an Android-based phone instead. Not that doing any random Android hack is easy, but at least the platform is much more open, there is a much larger community and know-how pool around it, and for many things you can actually just write a regular app with widely available tools, and install it with just a few clicks. You cannot do that on a Nucleus phone!
Now that we got that out of the way, we can get a bit more technical. To do the simplest hacks, it suffices that you are entirely familiar with how to use computers. To do the most difficult hacks, you need to be familiar with electronics and low-level software concepts, in other words you must understand how computers work down to the low-level details. You have been warned.
Caution: there is a new series of cheap smartwatches based on the MT626xDA. The ‘D’ in the model number seems to signify that these chips are incapable of using more than 4MiB of ROM. To compensate for this, the ROM seems to be compressed, which makes these watches pretty much unhackable. The ROM can be downloaded, but looks like random junk. Do not buy these things, because they will still be full of bugs and there will be no possibility whatsoever to fix them. Yet another motivation to move to Android-based (watch) phones.
Intro
Everything written here is based on the experiences I had with hacking two models thoroughly. The first was the S9110 based on the MT6225 platform, the second is the MQ668 based on the MT6253 platform. The good news is that almost all older watch phones were based on MT6225, and many newer ones are based on MT6253, so the information on this page should help you out to hack many older and current watch phones.
You may have bumped into some Russian software (like ChinaResMan, China Editor, MTKMediaEditor, MTKore, MTK Rom Studio, …) that allows some pretty advanced hacks on Chinese phones, with a user interface that is relatively easy to use. You may also have noticed that these programs are quite expensive and protected with extensive encryption systems. The reason is that making those programs takes an enormous amount of time and those people do not want to see their work being copied for free. The problem with those programs is that they get outdated very quickly and will no longer work on any recent phone because MediaTek keeps on changing the firmware format, so do not waste your time looking for these programs. This document describes methods to hack these phones for free… but only if you ignore the “time is money” proverb.
General Structure
Before you start, it is essential to know the general structure of the device you are going to hack. A typical MT62xx-based phone roughly consists of the following hardware:
- A system-on-a-chip, e.g. MT6225 or MT6253
- On-board flash memory holding the operating system and filesystem (this could be built into the SoC chip, but for all practical purposes this doesn't matter)
- An LCD display
- A touch screen sensor, mounted on top of the LCD
- A loudspeaker
- A microphone
- Hardware buttons
- Antennas, most often only a GSM antenna and a Bluetooth antenna
- Other components, possibly Bluetooth hardware etc.
The only thing we really care about here is the on-board flash memory. It is divided into three main parts:
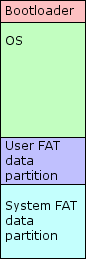 A bootloader that boots up the phone when it is powered on, and loads the operating system. This never changes during use and you should never ever touch this. If you mess this up, your phone becomes a useless brick.
A bootloader that boots up the phone when it is powered on, and loads the operating system. This never changes during use and you should never ever touch this. If you mess this up, your phone becomes a useless brick.- The operating system itself. This, as well as the bootloader, never changes during normal use.
- A FAT file system, much like what is on a typical USB stick. This changes over use. There are two important facts about this. First, it is typically divided into two partitions. The first is a user partition, the one you see when you plug the phone into your PC via a USB cable. This is often such a small partition (like 700kBytes) that it is nearly useless. The second however holds all the important system data that can change over time. The catch is that this partition is invisible because the phone only tells your computer that it has the user partition. Some phones may lack the user partition altogether, which can make it more difficult to reach the system partition.
The second important fact is that the phone will perform ‘wear levelling’ while updating these partitions, to avoid that the flash memory wears out quickly. What this means is that if you would copy the FAT partitions directly from the flash memory, they will be scrambled. The best way to obtain them is to download them through the phone's own USB connection as described below.
All the hacks described here will either be performed inside the hidden system file partition, or the operating system chunk. The first are the easier hacks, because all you need to perform them is the USB cable and the right software. Hacks within the OS are much harder, because first of all you need to be able to download the firmware image, which requires a special cable and a serial adaptor. And once you have this image, you have one big monolithic chunk of data that requires considerable skill to edit. Let me make one thing clear: hacking these phones is not for the faint of heart. Do not expect to just download a magical hacking tool that turns any crappy phone into a tiny iPhone on your wrist. You will need to get your hands dirty and require huge amounts of spare time.
Engineer Mode
Most of the MTK-based phones have an ‘Engineer mode’ that can be accessed by entering a special phone number. The number typically looks like *#36466336# or a variation with fewer or more digits, but it can be entirely different (e.g. on my MQ668 it was *#503#). Unfortunately the only reliable way to find the code for Engineer mode for a particular phone, is by downloading the ROM image and looking for strings that match the pattern: “*#[digits]#”. Do not be tempted to try all kinds of codes in a trial-and-error manner: there is generally also a particular code that disables Engineer mode, so if you would accidentally enter that code, you'd be locked out forever unless you can restore a previous backup of your ROM image.
Engineer mode is interesting because it may allow to perform some basic tweaks without requiring the types of hacks described below. How useful Engineer mode is on your particular phone, depends on what the makers of its ROM decided to put into it. It may be possible to adjust audio levels in it, or change the user-agent string of the browser. On my MQ668 however, Engineer mode was stripped of almost everything useful, so it is a bit of a matter of luck.
One thing you should remember when trying to change anything inside Engineer mode, is to stay clear of options you do not understand. It is possible to perform actions that will brick your phone, e.g. the ‘High speed SIM’ option is rumoured to cause instant brick (I never tried it, obviously). It is highly recommended to first make a ROM backup before trying anything special.
Next to Engineer mode, there is also Factory Mode, which offers all kinds of tests for the hardware of the phone. It is generally safe to play around in this, although some tests may cause you to get stuck and require a reboot of the phone. Again, the code for Factory mode may vary between phones, on my S9110 it was *#666*#, on the MQ668 it was *#504#.
FAT Partition-based Hacks
- General Way of Working
- File Checksums
- Loudspeaker Volume and Microphone Sensitivity
- Battery levels
- Other tidbits
General Way of Working
When I said that these are the easier
hacks, I did not mean they are easy, only that they are less difficult than the horribly difficult OS hacks. They are still hard and they require some knowledge about mounting file systems and editing binary data files. If you do not even know what ‘mounting’ means or what a file system is, then I suggest you give up right now and buy an iPhone while waiting until someone builds a decent non-frustrating watch phone. I will only provide the basics here and assume you can figure out how to do the technical stuff yourself. Mind that I am providing all this info here voluntarily and this is already taking a lot of my time I'd rather use for something else. If you mail me with questions, be patient. I will try to answer them but it could take time (a week will not be unusual).
The clue to these hacks lies within mounting the hidden system FAT partition. For Windows there are a few programs that allow to mount this partition (look for “Chinese Phone Suite”). There is a general method however that should always work for any operation system. I have only done it in Linux and Mac OS X, so any example commands I give below will be for those operating systems only. Please do not ask how to do this in Windows. After having gained experience with various different operating systems, my vision of Windows has become that it is a toy operating system only good for games, and that is the only thing I use it for.
- Turn off the phone and plug it into your PC with the USB cable. After the user partition has mounted, find its mount point (use the ‘
mount’ command). Then, unmount it again but do not unplug the phone. - Strip the partition number off the mount point you obtained in the previous step. E.g. if it was mounted on /dev/sdb1 (Linux), or /dev/disk1s1 (OS X), then what you need in the next step is respectively /dev/sdb and /dev/disk1.
- Use the ‘dd’ command to dump the entire device to a data file. E.g. “
dd if=/dev/sdb of=phone.dat”. By all means keep a backup copy of the very first dump you create this way, or the last one that worked flawlessly. If you mess things up, you can always restore this one. - Run ‘fdisk’ on the data file and create a new partition right after the existing one. Make it extend all to the end of the data file, and save the new partition table.
- Now mount the data file. In Mac OS X this is very easy: give it a file extension ‘.dmg’ and double-click the file. In Linux you'll have to create a loopback device and fiddle with the
losetupandmountcommands. - Do the hacks on the mounted file system. Mind the file checksums. Once you're ready, unmount the filesystems and do the inverse ‘dd’ command, for instance “
dd if=phone.dat of=/dev/sdb”. - Unplug the phone and power it on. The hack should now be applied.
If you are hoping that you can overwrite the partition table on the phone itself such that it always mounts the two partitions: nice try, but no cigar. The phone will overwrite your changes and always return the single-partition table, therefore the kludge described above is unavoidable.
In Linux there is a caveat with usb_modeswitch, which is something that tries to work around crap that manufacturers embed in some USB devices like modems to make them have multiple personalities. Phones will typically present themselves as a CD-ROM drive offering Windows drivers. It is possible that this will prevent the data partitions on the phone from mounting in Linux. Sometimes even weirder things may happen, like button press commands being sent to the phone.
If this happens, a quick but ugly workaround is to disable automatic switching in /etc/usb_modeswitch.conf.
A better fix is to add an exception rule for the USB vendor and device ID of your specific phone. To do this, create a file /etc/usb_modeswitch.d/0e8d:0002, replacing “0e8d:0002” with the vendor/product ID of your particular device (this example ID is a typical one for certain MediaTek devices). Inside this file, write the following line:
Configuration=0
File Checksums
Before you do any of these hacks, it is important to note that all the binary files end with a checksum calculated over the rest of the file. If the checksum is incorrect, the phone will replace the entire file with default values. So if you're going to modify these files without recalculating the checksum, your hacks will have no effect. Obviously, you will want to use a program to compute this checksum.
The checksum is stored in the last two bytes of every file. Assuming that the first byte in the file has an even index (0) and the second byte an odd index (1), the algorithm to compute the checksum is pretty simple. The second to last byte contains the sum of all preceding odd bytes modulo 256. The last byte contains the sum of all even bytes modulo 256. Or, in (straightforward but inefficient) code:
checksum = unsigned char[2];
checksum[0] = checksum[1] = 0;
for( i=0; i<filesize-2; i++ ) {
if( i & 0x1 )
checksum[0] += data[i];
else
checksum[1] += data[i];
}
Sorry, but I do not have a ready-to-use program that you can download. If you have basic programming skills in any language that allows low-level data operations (e.g. Python), you should be able to implement something that reads a file, performs the above loop, and either writes the checksum back to the file or prints it out so you can manually update it in a hex editor. If this looks scary already, you may want to consider throwing your Chinese phone in the trash and buying one of the newer rootable Android-based models which will not have stupid bugs and are much easier to customise.
Loudspeaker Volume and Microphone Sensitivity
MTK phones have the following audio modes (newer phones may have additional modes for Bluetooth etc.):
- Normal: this is the ‘hand-held’ mode, intended to be used while you are holding the phone near your ear.
- LoudSp: ‘hands-free’ mode, where the loudspeaker gets an extra boost and a more aggressive echo cancellation is used.
- Headset: used when a headset is connected (unsure whether it also applies to Bluetooth headsets, but it probably is).
Each mode has several separate volume settings that are used in specific situations. Each setting has 7 levels. They also define a ‘maximum analog gain’ and step size that are used inside the music and movie player (which offers a more fine-grained volume adjustment than 7 steps). The microphone also has a gain value. Even though it seems you can define a different microphone gain for each of the 7 loudspeaker gains, I believe only one value is actually used. It also makes almost no sense to vary the microphone gain, therefore I recommend using the same value for each of the 7 settings.
The Chinese have a tendency to mess up the volume and sensitivity settings. Mostly they don't seem to know what they are doing, and often they will turn down the microphone out of fear that it could cause feedback howl. It is often safe to boost the microphone level considerably or even set it to the maximum. If you do get a howling sound, turn down the Microphone values until it no longer occurs. For Normal and LoudSp, you should definitely set the “sidetone” values to zero. Sidetone determines how much of your own voice is played through your own speakers, and is useful for the Headset profile to better hear yourself speaking.
If you're lucky, these settings can be modified in the Engineer mode of your phone, but this is not always the case. The alternative is to directly edit them in the NVDATA file MP05_001. On the phones that I hacked, the structure of this file is as below. Each of the 7 volume levels is a single byte, as are the media max gain and step size.
MP05_001 file structure: 0x00-0x06: unknown, all 7F 0x07-0x0D: Normal Key Tone 0x0E-0x14: Normal Microphone 0x15-0x1B: Normal FM Radio 0x1C-0x22: Normal Speech 0x23-0x29: Normal Sidetone 0x2A-0x30: Normal Melody 0x31-0x37: unknown, all 7F 0x38-0x3E: Headset Key Tone 0x3F-0x45: Headset Microphone 0x46-0x4C: Headset FM Radio 0x4D-0x53: Headset Speech 0x54-0x5A: Headset Sidetone 0x5B-0x61: Headset Melody 0x62-0x68: unknown, all 7F 0x69-0x6F: LoudSp Key Tone 0x70-0x76: LoudSp Microphone 0x77-0x7D: LoudSp FM Radio 0x7E-0x84: LoudSp Speech 0x85-0x8B: LoudSp Sidetone 0x8C-0x92: LoudSp Melody 0x93-0xA7: unknown 0xA8: Normal Max Analog Gain 0xA9: Headset Max Analog Gain 0xAA: LoudSp Max Analog Gain 0xAB: unknown 0xAC: Normal Step 0xAD: Headset Step 0xAE: LoudSp Step 0xAF-0xB6: unknown 0xB7-0xB8: checksum
Battery levels
The pre-Android phones use a simple table that maps battery voltage to the battery indicator on the screen. The number of different levels that can be shown in the indicator, differs per phone firmware. However, the voltage-to-level map is most likely stored in the NVDATA file MP01_001, around 0x168 to 0x18F. The lowest voltage comes first. The first few levels all map to the ‘empty’ indicator but could trigger different kinds of low battery warning pop-ups. Each value is a 32-bit unsigned integer in little Endian format, representing microvolts (e.g. D8 15 35 00 is 3.479 Volts). It is not trivial to get good values for this table, check out my MQ668 review to get an idea of how it can be done. Basically, you should cause a steady drain on the battery (e.g. by looping a movie) and read out the voltage in Engineer mode at regular intervals to obtain the kind of curve shown there.
Other tidbits
The photo and video counter values can be in a file called either CT01_010 or MM01_001. The photo counter is at bytes 0x5C,0x5D and the video counter at 0x60-0x61.
The address book seems to be distributed across two files: MP0c_000 and MP0h_001. Telephone numbers are encoded with two digits per byte: the last four bits represent the first digit, and the first four bits the second digit.
Quick dial or voicemail settings are stored in MP13_001. This may be useful if you accidentally configured this on a phone that does not allow to undo this setting, as was the case on my MQ668. Just write some garbage to the file to cause it to be reverted to default.
Operating System Hacks
These hacks involve downloading the binary ROM image, editing the ROM dump, and then re-uploading it to the phone. The bad news is that the binary format tends to change between different phone models, which is why it is pointless to describe in detail how to perform a particular hack. Instead, I will explain the general way of working and give a few examples.
General way of working
Whatever you want to do, be it trying to simply flash another firmware or making some small hack, make a backup of your current ROM image first! It is a good idea anyhow because it allows to check whether the serial connection is reliable, but the most important thing is that you can go back to your old image if anything fails. Please don't mail me asking where you can find a ROM image to restore your random obscure smartwatch because you forgot to make a backup, I cannot help you with that.
First, you need to figure out how to make a direct serial connection to the phone. This could involve soldering your own cable, or disassembling the phone and probing contacts on the PCB (look for contacts marked ‘TX’ and ‘RX’. Only on very recent phones it might be possible to download through the standard USB cable.

If the phone has one of those typical 12-pin connectors as pictured on the right, or some other connector with more than 4 pins, there is a method that can be used to figure out what pins are likely to be the TX and RX of the serial connection. Both TX and RX pins will typically be at a specific voltage when the phone is turned on. If you short the pins to ground with a resistor of reasonable value, the RX pins will drop to near-zero Volts while the TX pins will keep their voltage. For more details, google around. You can find pin-outs for the S9110 and MQ668 in their respective reviews.
If you have found the TX and RX pins on either the connector or PCB, you need to connect them to your PC through a TTL-to-USB adaptor (not a RS232 serial port if your PC still has one of those, because it does not use TTL levels). I recommend using a TTL-to-USB adaptor based on the CP2102 chip. Once you have this hardware part figured out, you can move to the software:
- Download the MTK FlashTool program somewhere. I recommend the 3.1004 version if you are using a serial connection. Other versions may work better with certain phones.
- Turn off the phone, connect it to the PC, start the download process in FlashTool, and power on the phone. The ROM should now be downloaded to a file to your hard disk.
- Either buy one of those ridiculously expensive Russian MTK firmware hacking programs, or go to a university and get a degree in engineering or computer sciences.
- Open the binary ROM dump with your Russian program and hope it doesn't mess everything up, or open it with a hex editor and use your university education to figure out how it all fits together. <sarcasm>Have fun!</sarcasm>
- When ready, upload the modified ROM file back to your phone.
These steps skip various important details, so if you have no idea yet how to hack the firmware, they will be of little help. Like I said above, hacking these phones is not as simple as downloading an app or watching a YouTube video. There are almost no free tools. The binary formats inside the firmware are often proprietary and can change between firmware versions. You're pretty much on your own here. You need tons of patience. I pretty much burned up my entire lifetime stockpile of patience on these kinds of hacks, you have been warned.
Nevertheless, a lot of hacks simply involve searching for certain strings inside the ROM dump, and editing them with a hex editor. For instance, to avoid that the WAP browser has a preference for Chinese webpages, look for a string like “zh-tw, zh-cn, en” and replace it with anything that starts with “en” or your language code of choice, but make sure the new string is exactly as long as the original, pad it with spaces if necessary. This is essential: whatever you do, make sure to not delete or insert any bytes: everything must stay at the same address locations in the ROM.
Of course, the ROM image is not just a blob of random data. It has a logical structure and in theory it is possible to reverse engineer this structure and pull the ROM neatly apart into all its components. Some of the Russian programs partially allow to do this, but this functionality often breaks between different versions of the firmware.
One essential fact is that every data block in the ROM must be aligned to a multiple of 4 bytes (because this is a 32-bit platform). If you are looking for something in the big blob of binary data, and it is at an address divisible by 4, then it has a better chance of being the thing you're looking for than if it is at a random place. Parts of the ROM consist of tables that contain addresses pointing to data blocks. If you find a chunk in the ROM with a bunch of numbers that are divisible by 4, it is likely to be such table. The addresses may have an offset w.r.t. the actual data. One important lesson to remember from this, is that it is often possible to relocate data in a limited manner inside the ROM.
Example: you want to replace an image currently at address 0x931F38 with something larger. First, find some unused space in the ROM with room for the larger data: the last part right before the user data partition is a good candidate. Paste your image there at an address that is a multiple of 4. Next, search for the old address bytes in reverse order: 38 1F 93. If you find nothing, try again with 4 added or subtracted from the address. If you find occurrences of this address inside a regular-looking table, replace them with the new address of your image, again bytes reversed (and with offset if necessary). Now the phone will either work and use your new image, or do strange things and crash badly. The latter will happen if either what you modified was not really the address table, or the space where you have put your image was not unused. Unfortunately this method does not always work, sometimes the addresses in the tables are too different from the actual ROM positions, or the phone computes the address of the data without going through a table altogether.
Keyboard layout and background hack
To give you a taste of how these kind of low-level hacks are performed, I'll make all the information available that I gathered to perform the custom keyboard layout hack on the MQ668. I consider that hack the most difficult I have ever done. Because I suspect that the way in which the keyboards are represented might differ slightly or severely between different firmwares, it is pointless to make a step-by-step recipe for this kind of hack. Instead, I just provide my notes here for download, as well as a Perl script that is required to decode and encode the RLE background format. This is not for the faint of heart, but if you read through the notes and look at the examples, you should be able to perform the same kind of fix, even on other phones where the format differs somewhat.
- My notes from reverse engineering the MT6253 keyboards
- The Perl script that encodes and decodes the RLE-encoded keyboard backgrounds
- An example of the original and hacked keyboard parts from the MQ668 (zip file)
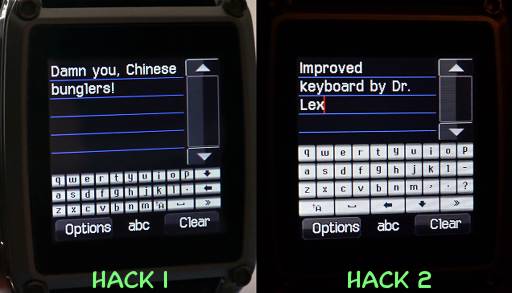
Older phones like the S9110 use a much simpler bitmap format for the keyboard backgrounds. It starts with 0x28 0x01, then a 16-bit integer indicating the size of the file minus 8, then 50 bytes of header data (including colour table, haven't reverse-engineered this). Then the actual bitmap follows, which is represented by 4 bits per pixel in little Endian, e.g. a byte 0xC1 means a pixel of colour index 1, followed by one of colour index C.
Browser user-agent
It seems relatively unknown that despite the primitive nature of these Nucleus OS-based phones, they are quite usable for basic internet browsing, at least when one has managed to configure the data connection. The main problem is that the built-in browser has to make do with very little RAM and other limitations. A solution is to browse through Google's ‘Wireless Transcoder’ as explained in the S9110 review. This will only work well if the browser identifies itself with an appropriate User-Agent HTTP header (and if Google haven't terminated their transcoder in the meantime).
If you are lucky, Engineer mode allows to change the User-Agent like on the S9110. Otherwise, you must edit the hard-coded string in the ROM itself, as I did with the MQ668. To do this, you must know where the User-Agent header string is in the ROM, in other words what string it is. This is easy if you have a web server reachable through the Internet: visit one of its webpages through the phone, then look in the server logs what user-agent it was. Or try to load a website that shows request headers in the phone's browser. Otherwise, try a case-insensitive search for “Maui Browser”, chances are good this is the default. Once you have found the current User-Agent string, you can modify it. I recommend the following string; beware that this will most likely be longer than the original and will therefore need to be relocated:
SonyEricssonK700i/R2AG SEMC-Browser/4.0.3 Profile/MIDP-1.0 MIDP-2.0 Configuration/CLDC-1.1
Browser CSS hacks
Here's another example of a hack: on the MQ668, the browser proved to have decent CSS support. This allowed to work around some of the most annoying problems like the ridiculously thick horizontal scroll bar appearing for no good reason. The browser has a master CSS file stored somewhere in the ROM. Finding this is relatively easy: just search for typical CSS syntax like “font-size”. When editing the CSS, the only thing you need to take care of, is to keep the file the exact same size as the original. Just pad it with newlines if your modified file is smaller, and ensure it is not larger. If it really needs to be larger, again you could try to move it to an unused section of the ROM.
In this particular case, I imposed some restrictions on the width of certain elements, such that they would never be wider than the available space in the tiny display. This prevented the horizontal scroll bar from appearing in e.g. the Google wap transcoder pages. Obviously, you must know something about CSS to do this kind of tweak. If you want to see how I tweaked the MQ668 CSS file, here is the original file versus my hacked file.